Strengthening Cybersecurity
with Penetration Testing
Cyberattacks have become one of the most significant threats facing organisations today. From ransomware and data breaches to phishing and insider threats, the digital landscape is rife with risks. As companies continue to embrace cloud computing, remote work, Internet-of-Things (IoT) devices, and complex web applications, their attack surface – the potential entry points for malicious actors – expands dramatically.
This evolving reality makes traditional security measures, such as firewalls and antivirus software, insufficient on their own. They remain vital, but they’re no longer enough. Today, proactive security testing is essential – and this is where penetration testing (pen testing) comes into play.
Penetration testing, often referred to as ethical hacking or white-hat hacking, goes beyond automated scans and basic audits. It simulates real-world cyberattacks on your systems to uncover vulnerabilities before attackers exploit them. Think of it as hiring a “friendly hacker” to break into your network – not to cause harm, but to expose weaknesses and help you fix them.
In this comprehensive guide, we’ll explore what penetration testing is, why it’s indispensable for modern organisations, the different types of tests available, and how to integrate it into your cybersecurity strategy.
What Is Penetration Testing?
Penetration testing is a simulated cyberattack performed by skilled security professionals – known as ethical hackers – against an organisation’s IT infrastructure, applications, and networks. The goal is to uncover security gaps, configuration issues, and exploitable weaknesses under controlled conditions.
Unlike vulnerability scanning, which is typically automated and provides a list of potential issues, penetration testing is manual and adversarial in nature. It replicates the tactics, techniques, and procedures (TTPs) used by real cybercriminals, providing a far more accurate picture of how secure your systems truly are.
Key Objectives of Penetration Testing
- Identify vulnerabilities before attackers do.
- Validate existing security controls and determine if they can withstand real-world attacks.
- Assess the impact of potential breaches, including how far an attacker could penetrate.
- Measure detection and response capabilities, revealing whether your security team can spot and contain threats.
- Provide actionable remediation recommendations to strengthen overall security posture.
Why Penetration Testing Matters in Today’s Threat Landscape
Cybercrime is not only increasing — it’s becoming more sophisticated. According to multiple industry reports, global cybercrime damages are projected to cost the world $10.5 trillion annually by 2025, making it more profitable than the global drug trade.
Here’s why penetration testing is no longer optional but essential:
1. Attackers are constantly evolving: New vulnerabilities and zero-day exploits emerge daily. Pen testing helps organisations stay ahead by identifying weaknesses proactively.
2. Compliance requirements: Many regulations — including ISO 27001, PCI DSS, HIPAA, and GDPR — mandate regular penetration testing as part of compliance.
3. Business continuity: A single breach can cripple operations, damage brand reputation, and erode customer trust. Pen testing helps prevent catastrophic incidents.
4. Third-party risks: As businesses increasingly rely on third-party software and cloud providers, penetration testing verifies the security of external integrations and dependencies.
5. Investor and customer confidence: Demonstrating that your organisation actively tests and strengthens its security defences builds trust with stakeholders.
Key Benefits of Penetration Testing
1. Uncover Hidden Vulnerabilities
Pen testers often find vulnerabilities that automated tools miss – such as complex logic flaws, misconfigurations, or chained exploits. These insights help organisations address real-world risks rather than relying solely on theoretical vulnerabilities.
2. Prevent Financial and Reputational Loss
The average cost of a data breach now exceeds USD $4.45 million (IBM, 2023). Penetration testing significantly reduces the likelihood of such incidents by ensuring that vulnerabilities are patched before they’re exploited.
3. Validate Security Controls
Firewalls, intrusion detection systems (IDS), multi-factor authentication (MFA), and endpoint protection tools are only as good as their configuration. Pen testing validates whether these defences function as intended under active attack conditions.
4. Enhance Incident Response Readiness
A simulated attack helps your security team test detection, response, and escalation processes. It exposes weaknesses in monitoring and incident handling – insights that can dramatically reduce response times during a real attack.
5. Support Compliance and Auditing
Most major cybersecurity standards recommend or require regular penetration testing. By conducting these assessments, you not only improve security but also streamline audits and demonstrate due diligence to regulators and partners.
6. Build a Security-First Culture
Penetration testing isn’t just a technical exercise – it’s a cultural shift. It helps employees and leadership understand the reality of cyber risk, fostering a proactive mindset around security across the organisation.
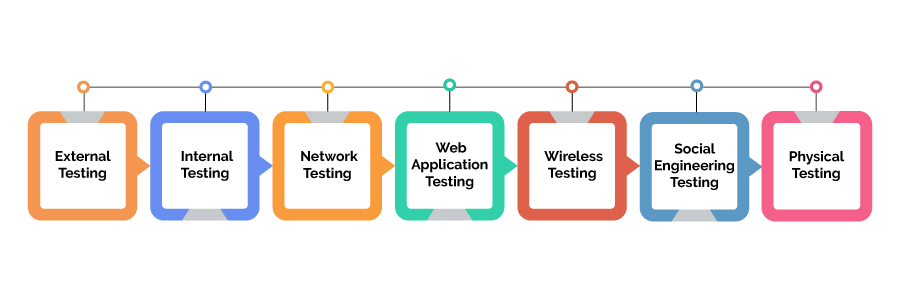
Types of Penetration Testing
Not all penetration tests are the same. The right approach depends on your infrastructure, business goals, and threat model. Below are the main types of penetration tests organisations typically use:
1. External Penetration Testing
Objective: Assess how attackers could breach your systems from the outside.
This test targets externally facing assets such as websites, firewalls, email servers, and public cloud environments. It simulates the actions of a remote hacker attempting to gain access to internal networks or sensitive data.
2. Internal Penetration Testing
Objective: Identify threats that originate inside the network.
This test assumes an attacker has already gained internal access – for example, through a compromised account or malicious insider. It focuses on lateral movement, privilege escalation, and internal network security gaps.
3. Network Penetration Testing
Objective: Evaluate the security of wired and wireless networks.
Network pen tests assess routers, switches, firewalls, VPNs, and other infrastructure components. The goal is to discover misconfigurations, weak encryption, default credentials, and other exploitable flaws.
4. Web Application Penetration Testing
Objective: Find vulnerabilities in web applications before attackers do.
This is one of the most critical tests, as web apps are a prime target for attacks such as SQL injection, cross-site scripting (XSS), broken authentication, and insecure direct object references (IDOR).
5. Wireless Penetration Testing
Objective: Ensure wireless networks cannot be exploited as entry points.
Wireless tests assess the security of Wi-Fi networks, access points, and protocols. They often reveal misconfigured SSIDs, weak encryption, or unauthorised devices.
6. Social Engineering Testing
Objective: Assess human vulnerability to manipulation.
Since people are often the weakest link, social engineering tests simulate phishing, pretexting, or baiting attacks to measure employee awareness and training effectiveness.
7. Physical Penetration Testing
Objective: Test physical security controls.
This advanced form of pen testing involves attempts to gain physical access to secure locations, bypass access controls, or manipulate hardware – often used in high-security environments.
The Penetration Testing Lifecycle
Understanding how a penetration test unfolds can help organisations better prepare and integrate findings into their cybersecurity strategy. A typical pen testing lifecycle follows these stages:
1. Planning and Scoping
The process begins by defining the scope, objectives, and boundaries of the test. This includes identifying the systems, applications, or networks to be tested and agreeing on rules of engagement.
2. Reconnaissance
Pen testers gather as much information as possible about the target environment. This could include public domain information (OSINT), network mapping, DNS enumeration, and more.
3. Vulnerability Discovery
The team identifies potential vulnerabilities through manual inspection and automated scanning. These findings form the basis for targeted exploitation attempts.
4. Exploitation
Ethical hackers attempt to exploit vulnerabilities just like a real attacker would – but without causing damage. This step helps assess the severity and real-world impact of discovered flaws.
5. Post-Exploitation and Privilege Escalation
After initial access is gained, testers attempt to escalate privileges, move laterally within the network, and access sensitive data. This phase shows how deep an attacker could go once inside.
6. Reporting and Remediation
Finally, the team delivers a detailed report outlining vulnerabilities, exploitation paths, potential business impact, and step-by-step remediation recommendations.
Best Practices for Implementing Penetration Testing
To get the most value from penetration testing, organisations should follow these best practices:
1. Test regularly: Penetration testing should be performed at least annually, and after major infrastructure changes, new application deployments, or mergers/acquisitions.
2. Adopt a risk-based approach: Prioritise testing for systems that store sensitive data, support critical business operations, or are publicly accessible.
3. Engage qualified professionals: Always work with certified penetration testers (e.g., OSCP, CEH, GPEN) or reputable cybersecurity firms.
4. Integrate with vulnerability management: Use penetration test results to enhance ongoing vulnerability scanning, patching, and monitoring programs.
5. Simulate diverse scenarios: Combine different types of tests (external, internal, social engineering) to get a complete view of your security posture.
6. Remediate and retest: Address all identified vulnerabilities promptly and conduct follow-up tests to ensure issues are fully resolved.
Getting Started with Penetration Testing
If your organisation has never conducted a penetration test, the process may seem daunting – but it doesn’t have to be. Here’s a straightforward roadmap:
1. Assess your security maturity: Identify key assets, data, and systems that require protection.
2. Define clear objectives: Determine whether you’re testing regulatory compliance, internal readiness, or overall security posture.
3. Select a trusted provider: Partner with a cybersecurity firm that specialises in penetration testing and understands your industry’s unique challenges.
4. Collaborate closely: Work with the testers to define scope, schedule testing activities, and ensure minimal business disruption.
5. Act on results: Treat the penetration test report as a strategic roadmap – not just a compliance checkbox. Implement fixes, strengthen policies, and update training accordingly.
Conclusion
In a world where cyber threats are relentless, penetration testing is not a luxury – it’s a necessity. It offers organisations a clear, actionable view of their security posture, revealing weaknesses before they become catastrophic breaches. By proactively identifying vulnerabilities, validating defences, and improving incident response capabilities, pen testing plays a critical role in building cyber resilience.
Investing in regular, comprehensive penetration testing demonstrates due diligence to customers, partners, and regulators – but more importantly, it protects your data, your reputation, and your business’s future.
In this article, I have looked at what penetration testing is, the goals it aims to achieve, its benefits and how organisations can get started with pen testing. By taking the necessary steps to protect their systems and infrastructure through penetration testing, organisations can ensure that they remain secure against potential cyber threats.
Please see this page: https://computingaustralia.com.au/penetration-testing/
Contact Chris on 0438 855 884 or email sales@computingaustralia.group

Chris Karapetcoff
FAQ
How does penetration testing simulate real-world cyberattacks?
Penetration testing mimics the methods and techniques used by actual cybercriminals to infiltrate a system. Ethical hackers attempt to exploit known and unknown vulnerabilities in the same way a malicious actor would, helping organisations identify weaknesses and address them before they’re exploited in real-life scenarios.
Can penetration testing help in preventing data breaches?
Yes, penetration testing helps organisations identify potential entry points and weak spots in their systems, allowing them to address vulnerabilities before they can be exploited in a data breach. By uncovering hidden flaws, penetration tests serve as a proactive approach to protect sensitive data.
How can penetration testing assist in improving employee security awareness?
Penetration testing, especially social engineering tests like phishing, helps raise awareness about human vulnerabilities. Employees are directly tested on their ability to identify suspicious activities, helping businesses improve security training and reduce the risk of human error leading to breaches.
What role does penetration testing play in meeting compliance standards?
Many industry standards and regulations, such as HIPAA, GDPR, and PCI DSS, require regular penetration testing to ensure the integrity and security of sensitive data. Pen testing helps businesses meet these compliance standards, avoid penalties, and demonstrate due diligence in protecting data.
Can penetration testing reveal unknown vulnerabilities in legacy systems?
Yes, penetration testing is especially valuable for uncovering vulnerabilities in older or legacy systems. These systems may not have received updates or security patches in a while, making them highly susceptible to exploitation. Penetration tests can highlight these issues and help modernise security strategies for such systems.


